

Enabling Access Control Services to connect to Multi Factor Authentication
From breaking down complex technical issues, through to revealing key benefits of the latest release of our awarding-winning ERP software, our series of technical blog posts will keep you regularly updated with all the information you need!

Last month we introduced you to our new blog series – designed to keep you updated on all manner of complex technical issues. In this next blog post from our technical support team, we’re learning all about how to enable access control services to connect to multi factor authentication.
Did you know that there are multiple ways to authenticate users in Microsoft Dynamics Nav/Business Central on Premise?
By default, users are authenticated using their Windows domain credentials, for example, DOMAIN\USERNAME – Wouldn’t it be nice if we could secure access to our data through Microsoft 365 and link this to Multi Factor Authentication?
Fortunately, this ability exists on any version of Microsoft Dynamics Nav/Business Central 2013 and upwards.
So, how do we achieve this?
On the Service Tier(s) for your environment, there is a configuration option for authentication called Credential Type, which dictates the authentication method used between the end user/client and the SQL database.
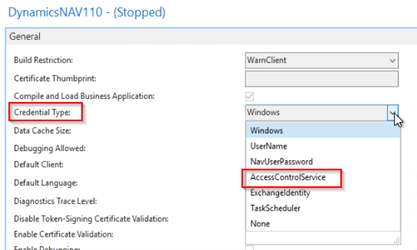
This needs to be set to AccessControlService so that when authenticating, Microsoft 365 is used.
Is there anything else we need to enable authentication via Microsoft 365?
There are a few more steps that you will need to follow:
- SSL Certificate – To secure the service, a Certificate Thumbprint is required from an SSL certificate, installed on the Service Tier.
- Azure App Registration – To link the service to the correct Azure Active Directory, an App Registration is required. Variables from the app are held against the service tier, more details can be found here – User Authentication with Azure AD for Single Sign-on – Business Central | Microsoft Docs
- An Exposed Port and DNS rule– As the service tier will need to speak to Azure to confirm the user identify, a secure DNS rule and exposed port are needed for HTTPS traffic.
Once these steps have been taken, your end users will be able to authenticate using their Microsoft 365 account, adding an additional layer of security to your environment.
Want to know more?
If you have any questions about authentication using Microsoft 365 accounts, then get in touch with your technical support team for more information.
Don’t forget to check back regularly for further technical updates and if there’s anything you’d like to see covered on the blog in the future, then let us know!

About the author
David McFall | David is one of 4PS’ Technical Consultants, dealing with customers to improve system performance and technical understanding, allowing them to make the most of 4PS Construct.
